The whole business of climate change has been a political and scientific football over the past decade, with assertions and counter assertions and predictions and counter predictions flying all over the place. There’s a lot of research money and many reputations at stake, so the struggle has been serious, but neither of the major positions on both sides of the argument for anthropogenic global warming are telling you the whole truth.
There are a lot of rather extraordinary, fascinating converging forces in play – including a thinning of our atmosphere, a decrease in solar activity and the accelerating trend toward a planetary magnetic pole shift that fly in the face of the usual arguments that humans are causing global warming or that this is all just a ruse by the government to take more of our money through things like carbon taxes. The truth is much bigger than that and you should understand what is happening.
For the last six months I have been collecting everything that I can find on the climate change subject and building a coherent picture (to me, at least) of what is really going on. I’ll be laying out the whole picture in a Transition Talk on Saturday the 26th of October at 3:00 PM at the Ice House here in Berkeley Springs, West Virginia. There will be lots of slides and graphics that help to present a comprehensive image of all of the moving parts, where they seem to be going and what we probably should be doing about it. Hint: it’s really big stuff. More info here.
I hope that you will be able to join us. It will be a good afternoon. Come and spend the weekend and enjoy our town’s warm hospitality.
Government Is Spying On Us Through Our Computers, Phones, Cars, Buses, Streetlights, at Airports and On The Street, Via Mobile Scanners and Drones, Through Our Smart Meters, and In Many Other Ways
Security expert Bruce Schneier confirms what we’ve been saying for years … don’t get too distracted by the details, because the government is spying on everything:
Honestly, I think the details matter less and less. We have to assume that the NSA has EVERYONE who uses electronic communications under CONSTANT surveillance. New details about hows and whys will continue to emerge — for example, now we know the NSA’s repository contains travel data — but the big picture will remain the same.
John Lanchester writes in the Guardian:
This is the central point about what our spies and security services can now do. They can, for the first time, monitor everything about us, and they can do so with a few clicks of a mouse and – to placate the lawyers – a drop-down menu of justifications.
As shown below, Schneier and Lanchester are right.
The NSA is tapping the very backbone of the Internet. It then stores metadata on everyone for up to a year.
As the New York Times reported this week, the NSA is also constructing sophisticated graphs of our social connections:
Since 2010, the National Security Agency has been exploiting its huge collections of data to create sophisticated graphs of some Americans’ social connections that can identify their associates, their locations at certain times, their traveling companions and other personal information, according to newly disclosed documents and interviews with officials.
The spy agency began allowing the analysis of phone call and e-mail logs in November 2010 to examine Americans’ networks of associations for foreign intelligence purposes after N.S.A. officials lifted restrictions on the practice, according to documents provided by Edward J. Snowden, the former N.S.A. contractor.
***
The agency can augment the communications data with material from public, commercial and other sources, including bank codes, insurance information, Facebook profiles, passenger manifests, voter registration rolls and GPS location information, as well as property records and unspecified tax data, according to the documents. They do not indicate any restrictions on the use of such “enrichment” data, and several former senior Obama administration officials said the agency drew on it for both Americans and foreigners.
***
The decision to revise the limits concerning Americans was made in secret, without review by the nation’s intelligence court or any public debate. As far back as 2006, a Justice Department memo warned of the potential for the “misuse” of such information without adequate safeguards.
***
The agency has multiple collection programs and databases, the former officials said, adding that the social networking analyses relied on both domestic and international metadata.
***
A series of agency PowerPoint presentations and memos describe how the N.S.A. has been able to develop software and other tools — one document cited a new generation of programs that “revolutionize” data collection and analysis — to unlock as many secrets about individuals as possible.
***
Phone and e-mail logs, for example, allow analysts to identify people’s friends and associates, detect where they were at a certain time, acquire clues to religious or political affiliations, and pick up sensitive information like regular calls to a psychiatrist’s office, late-night messages to an extramarital partner or exchanges with a fellow plotter.
“Metadata can be very revealing,” said Orin S. Kerr, a law professor at George Washington University. “Knowing things like the number someone just dialed or the location of the person’s cellphone is going to allow them to assemble a picture of what someone is up to. It’s the digital equivalent of tailing a suspect.”
***
The N.S.A. performed the social network graphing in a pilot project for 1 ½ years “to great benefit,” according to the 2011 memo.
***
In the 2011 memo explaining the shift, N.S.A. analysts were told that they could trace the contacts of Americans as long as they cited a foreign intelligence justification. That could include anything from ties to terrorism, weapons proliferation or international drug smuggling to spying on conversations of foreign politicians, business figures or activists. [This definition is so broad that knowing a cheese maker in France or a climate activist in England could drag an American into the NSA surveillance net.]
**
The documents show that significant amounts of information from the United States go into Mainway. An internal N.S.A. bulletin, for example, noted that in 2011 Mainway was taking in 700 million phone records per day. In August 2011, it began receiving an additional 1.1 billion cellphone records daily from an unnamed American service provider ….
***
The budget document, disclosed by Mr. Snowden, shows that the agency is pouring money and manpower into creating a metadata repository capable of taking in 20 billion “record events” daily and making them available to N.S.A. analysts within 60 minutes.
***
A top-secret document titled “Better Person Centric Analysis” describes how the agency looks for 94 “entity types,” including phone numbers, e-mail addresses and IP addresses. In addition, the N.S.A. correlates 164 “relationship types” to build social networks and what the agency calls “community of interest” profiles, using queries like “travelsWith, hasFather, sentForumMessage, employs.”
A 2009 PowerPoint presentation provided more examples of data sources available in the “enrichment” process, including location-based services like GPS and TomTom, online social networks, billing records and bank codes for transactions in the United States and overseas.
***
If the N.S.A. does not immediately use the phone and e-mail logging data of an American, it can be stored for later use, at least under certain circumstances, according to several documents.
An internal briefing paper from the N.S.A. Office of Legal Counsel showed that the agency was allowed to collect and retain raw traffic, which includes both metadata and content, about “U.S. persons” for up to five years online and for an additional 10 years offline for “historical searches.”
The NSA chief and Director of Intelligence have largely confirmed the program.
The government is spying on you through your phone … and may even remotely turn on your camera and microphone when your phone is off.
As one example, the NSA has inserted its code into Android’s operating system — bugging three-quarters of the world’s smartphones. Google – or the NSA – can remotely turn on your phone’s camera and recorder at any time.
Moreover, Google knows just about every WiFi password in the world … and so the NSA does as well, since it spies so widely on Google.
But it’s not just the Android. In reality, the NSA can spy on just about everyone’s smart phone.
Cell towers track where your phone is at any moment, and the major cell carriers, including Verizon and AT&T, responded to at least 1.3 million law enforcement requests for cell phone locations and other data in 2011. (And – given that your smartphone routinely sends your location information back to Apple or Google – it would be child’s play for the government to track your location that way.) Your iPhone, or other brand of smartphone is spying on virtually everything you do (ProPublica notes: “That’s No Phone. That’s My Tracker“). Remember, that might be happening even when your phone is turned off.
The NSA has gathered all of that cellphone location information.
The government might be spying on you through your computer’s webcam or microphone. The government might also be spying on you through the “smart meter” on your own home.
NSA also sometimes uses “man-in-the-middle” tactics, to pretend that it is Google or other popular websites to grab your information.
The FBI wants a backdoor to all software. But leading European computer publication Heise said in 1999 that the NSA had already built a backdoor into all Windows software.
Microsoft has long worked hand-in-hand with the NSA and FBI so that encryption doesn’t block the government’s ability to spy on users of Skype, Outlook, Hotmail and other Microsoft services.
And Microsoft informs intelligence agencies of with information about bugs in its popular software before it publicly releases a fix, so that information can be used by the government to access computers. (Software vulnerabilities are also sold to the highest bidder.)
A top expert in the ‘microprocessors’ or ‘chips’ inside every computer – having helped start two semiconductor companies and a supercomputer firm – also says:
He would be “surprised” if the US National Security Agency was not embedding “back doors” inside chips produced by Intel and AMD, two of the world’s largest semiconductor firms, giving them the possibility to access and control machines.
***
[The expert] said when he learned the NSA had secured “pre-encryption stage” access to Microsoft’s email products via the PRISM leaks, he recognised that “pretty much all our computers have a way for the NSA to get inside their hardware” before a user can even think about applying encryption or other defensive measures.
Leading security experts say that the NSA might have put a backdoor in all encryption standards years ago. … meaning that the NSA could easily hack into all encrypted communications. And the NSA hacks into encrypted “VPN” connections, and TOR.
It’s gotten so bad that some of the largest encryption companies are warning that their encryption tools are compromised.
“Black boxes” are currently installed in between 90% and 96% of all new cars. And starting in 2014, all new cars will include black boxes that can track your location.
License plate readers mounted on police cars allow police to gather millions of records on drivers … including photos of them in their cars.
If you have a microphone in your car, that might also open you up to snoopers. As CNET points out:
Surreptitious activation of built-in microphones by the FBI has been done before. A 2003 lawsuit revealed that the FBI was able to surreptitiously turn on the built-in microphones in automotive systems like General Motors’ OnStar to snoop on passengers’ conversations.
When FBI agents remotely activated the system and were listening in, passengers in the vehicle could not tell that their conversations were being monitored.
A security expert and former NSA software developer says that hackers can access private surveillance cameras. Given that the NSA apparently already monitors public cameras using facial recognition software (and see this), and that the FBI is building a system which will track “public and private surveillance cameras around the country”, we can assume that government agencies might already be hacking into private surveillance cameras.
The CIA wants to spy on you through your dishwasher and other “smart” appliances. As Slate notes:
Watch out: the CIA may soon be spying on you—through your beloved, intelligent household appliances, according to Wired.
In early March, at a meeting for the CIA’s venture capital firm In-Q-Tel, CIA Director David Petraeus reportedly noted that “smart appliances” connected to the Internet could someday be used by the CIA to track individuals. If your grocery-list-generating refrigerator knows when you’re home, the CIA could, too, by using geo-location data from your wired appliances, according to SmartPlanet.
“The current ‘Internet of PCs’ will move, of course, toward an ‘Internet of Things’—of devices of all types—50 to 100 billion of which will be connected to the Internet by 2020,” Petraeus said in his speech. He continued:
Items of interest will be located, identified, monitored, and remotely controlled through technologies such as radio-frequency identification, sensor networks, tiny embedded servers, and energy harvesters—all connected to the next-generation Internet using abundant, low cost, and high-power computing—the latter now going to cloud computing, in many areas greater and greater supercomputing, and, ultimately, heading to quantum computing.
***
ITworld’s Kevin Fogarty thinks that J. Edgar Hoover, were he still with us, would “die of jealousy” upon hearing about the tools soon to be at Petraeus’ disposal.
And they’re probably bluffing and exaggerating, but the Department of Homeland Security claims they will soon be able to know your adrenaline level, what you ate for breakfast and what you’re thinking — from 164 feet away. (In addition, people will probably soon be swallowing tracking devices for medical purposes)
The government is allegedly scanning prisoners’ brains without their consent at Guantanamo. In the near future, brain scanners may be able to literally read our thoughts (and see this).
The government is currently testing systems for use in public spaces which can screen for “pre-crime”. As Nature reports:
Like a lie detector, FAST measures a variety of physiological indicators, ranging from heart rate to the steadiness of a person’s gaze, to judge a subject’s state of mind. But there are major differences from the polygraph. FAST relies on non-contact sensors, so it can measure indicators as someone walks through a corridor at an airport, and it does not depend on active questioning of the subject.
CBS News points out:
FAST is designed to track and monitor, among other inputs, body movements, voice pitch changes, prosody changes (alterations in the rhythm and intonation of speech), eye movements, body heat changes, and breathing patterns. Occupation and age are also considered. A government source told CNET that blink rate and pupil variation are measured too.
A field test of FAST has been conducted in at least one undisclosed location in the northeast. “It is not an airport, but it is a large venue that is a suitable substitute for an operational setting,” DHS spokesman John Verrico told Nature.com in May.
Although DHS has publicly suggested that FAST could be used at airport checkpoints–the Transportation Security Administration is part of the department, after all–the government appears to have grander ambitions. One internal DHS document (PDF) also obtained by EPIC through the Freedom of Information Act says a mobile version of FAST “could be used at security checkpoints such as border crossings or at large public events such as sporting events or conventions.”
The risk of false positives is very real. As Computer World notes:
Tom Ormerod, a psychologist in the Investigative Expertise Unit at Lancaster University, UK, told Nature, “Even having an iris scan or fingerprint read at immigration is enough to raise the heart rate of most legitimate travelers.” Other critics have been concerned about “false positives.” For example, some travelers might have some of the physical responses that are supposedly signs of mal-intent if they were about to be groped by TSA agents in airport security.
Various “pre-crime” sensing devices have already been deployed in public spaces in the U.S.
The government has also worked on artificial intelligence for “pre-crime” detection on the Web. And given that programs which can figure out your emotions are being developed using your webcam, every change in facial expression could be tracked.
According to the NSA’s former director of global digital data – William Binney – the NSA’s new data storage center in Utah will have so much storage capacity that:
“They would have plenty of space … to store at least something on the order of 100 years worth of the worldwide communications, phones and emails and stuff like that,” Binney asserts, “and then have plenty of space left over to do any kind of parallel processing to try to break codes.”
***
[But the NSA isn’t stopping there.] Despite its capacity, the Utah center does not satisfy NSA’s data demands. Last month, the agency broke ground on its next data farm at its headquarters at Ft. Meade, Md. But that facility will be only two-thirds the size of the mega-complex in Utah.
The NSA is building next-generation quantum computers to process all of the data.
NBC News reports:
NBC News has learned that under the post-9/11 Patriot Act, the government has been collecting records on every phone call made in the U.S.
This includes metadata … which can tell the government a lot about you. And it also includes content.
The documents leaked by Edward Snowden to Glenn Greenwald show:
But what we’re really talking about here is a localized system that prevents any form of electronic communication from taking place without its being stored and monitored by the National Security Agency.
It doesn’t mean that they’re listening to every call, it means they’re storing every call and have the capability to listen to them at any time, and it does mean that they’re collecting millions upon millions upon millions of our phone and email records.
In addition, a government expert told the Washington Post that the government “quite literally can watch your ideas form as you type.” (And see this.) A top NSA executive confirmed to Washington’s Blog that the NSA is intercepting and storing virtually all digital communications on the Internet.
McClatchy notes:
FBI Director Robert Mueller told a Senate committee on March 30, 2011, that “technological improvements” now enable the bureau “to pull together past emails and future ones as they come in so that it does not require an individualized search.”
The administration is building a facility in a valley south of Salt Lake City that will have the capacity to store massive amounts of records – a facility that former agency whistleblowers say has no logical purpose if it’s not going to be a vault holding years of phone and Internet data.
***
Thomas Drake, a former NSA senior executive who challenged the data collection for several years, said the agency’s intent seems obvious.
“One hundred million phone records?” he asked in an interview. “Why would they want that each and every day? Of course they’re storing it.”
***
Lending credence to his worries, The Guardian’s latest report quoted a document in which Alexander purportedly remarked during a 2008 visit to an NSA intercept station in Britain: “Why can’t we collect all the signals all the time?”
***
One former U.S. security consultant, who spoke on condition of anonymity to protect his connections to government agencies, told McClatchy he has seen agency-installed switches across the country that draw data from the cables.
“Do I know they copied it? Yes,” said the consultant. “Do I know if they kept it? No.”
NSA whistleblower Russel Tice – a key source in the 2005 New York Times report that blew the lid off the Bush administration’s use of warrantless wiretapping – says that the content and metadata of all digital communications are being tapped by the NSA.
The NSA not only accesses data directly from the largest internet companies, it also sucks up huge amounts of data straight from undersea cables providing telephone and Internet service to the United States.
After all, the government has secretly interpreted the Patriot Act so that “everything” is deemed relevant … so the government can spy on everyone.
The NSA isn’t the only agency which is conducting massive spying.
The Wall Street Journal notes:
The rules now allow the little-known National Counterterrorism Center to … copy entire government databases—flight records, casino-employee lists, the names of Americans hosting foreign-exchange students and many others. The agency has new authority to keep data about innocent U.S. citizens for up to five years, and to analyze it for suspicious patterns of behavior. Previously, both were prohibited. Data about Americans “reasonably believed to constitute terrorism information” may be permanently retained.
The changes also allow databases of U.S. civilian information to be given to foreign governments for analysis of their own. In effect, U.S. and foreign governments would be using the information to look for clues that people might commit future crimes.
“It’s breathtaking” in its scope, said a former senior administration official familiar with the White House debate.
Reason notes:
Gazillions. That’s the number of times the federal government has spied on Americans since 9/11 through the use of drones, legal search warrants, illegal search warrants, federal agent-written search warrants and just plain government spying. This is according to Sen. Rand Paul, R-Ky., who, when he asked the government to tell him what it was doing to violate our privacy, was given a classified briefing. The senator — one of just a few in the U.S. Senate who believes that the Constitution means what it says — was required by federal law to agree not to reveal what spies and bureaucrats told him during the briefing.
Even if the US government weren’t recording all of that data, England’s GCHQ spy agency is … and is sharing it with the NSA.
Germany, Australia, Canada and New Zealand are also recording and sharing massive amounts of information with the NSA.
Private contractors can also view all of your data … and the government isn’t keeping track of which contractors see your data and which don’t. And because background checks regarding some contractors are falsified, it is hard to know the types of people that might have your information.
And top NSA and FBI experts say that the government can retroactively search all of the collected information on someone since 9/11 if they suspect someone of wrongdoing … or want to frame him.
The American government is in fact collecting and storing virtually every phone call, purchases, email, text message, internet searches, social media communications, health information, employment history, travel and student records, and virtually all other information of every American.
The Wall Street Journal reported that the NSA spies on Americans’ credit card transactions. Senators Wyden and Udall – both on the Senate Intelligence Committee, with access to all of the top-secret information about the government’s spying programs – write:
Section 215 of the Patriot Act can be used to collect any type of records whatsoever … including information on credit card purchases, medical records, library records, firearm sales records, financial information and a range of other sensitive subjects.
Many other government agencies track your credit card purchases as well. In fact, all U.S. intelligence agencies – including the CIA and NSA – are going to spy on Americans’ finances.
The IRS will be spying on Americans’ shopping records, travel, social interactions, health records and files from other government investigators.
The Consumer Financial Protection Board will also spy on the finances of millions of Americans.
As Washington Monthly noted in 2004, Congress chopped off the head of the Total Information Awareness program … but the program returned as a many-headed hydra:
A program can survive even when the media, the public, and most of Congress wants it killed. It turns out that, while the language in the bill shutting down TIA was clear, a new line had been inserted during conference—no one knew by whom—allowing “certain processing, analysis, and collaboration tools” to continue.
….Thanks to the Central Intelligence Agency and the National Security Agency, which had lobbied for the provision, TIA didn’t die—it metastasized. As the AP reported in February [of 2004], the new language simply outsourced many TIA programs to other intelligence offices and buried them in the so-called “black budget.” What’s more, today, several agencies are pursuing data mining projects independent of TIA, including the Department of Homeland Security, the Justice Department, the CIA, the Transportation Security Administration, and NASA….Even with TIA ostensibly shut down, many of the private contractors who worked on the program can continue their research with few controls.
The government is flying drones over the American homeland to spy on us. Indeed, the head of the FBI told Congress that drones are used for domestic surveillance … and that there are no rules in place governing spying on Americans with drones.
Senator Rand Paul correctly notes:
The domestic use of drones to spy on Americans clearly violates the Fourth Amendment and limits our rights to personal privacy.
Emptywheel notes in a post entitled “The OTHER Assault on the Fourth Amendment in the NDAA? Drones at Your Airport?”:
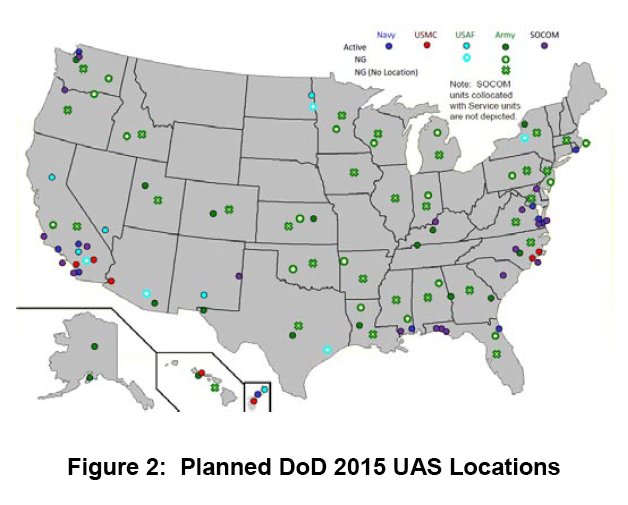
***
As the map above makes clear–taken from this 2010 report–DOD [the Department of Defense] plans to have drones all over the country by 2015.
Many police departments are also using drones to spy on us. As the Hill reported:
At least 13 state and local police agencies around the country have used drones in the field or in training, according to the Association for Unmanned Vehicle Systems International, an industry trade group. The Federal Aviation Administration has predicted that by the end of the decade, 30,000 commercial and government drones could be flying over U.S. skies.
***
“Drones should only be used if subject to a powerful framework that regulates their use in order to avoid abuse and invasions of privacy,” Chris Calabrese, a legislative counsel for the American Civil Liberties Union, said during a congressional forum in Texas last month.
He argued police should only fly drones over private property if they have a warrant, information collected with drones should be promptly destroyed when it’s no longer needed and domestic drones should not carry any weapons.
He argued that drones pose a more serious threat to privacy than helicopters because they are cheaper to use and can hover in the sky for longer periods of time.
A congressional report earlier this year predicted that drones could soon be equipped with technologies to identify faces or track people based on their height, age, gender and skin color.
The military is paying for the development of drones with facial recognition software which “remember” people’s faces … and read “malintent”.
Moreover, Wired reports:
Transit authorities in cities across the country are quietly installing microphone-enabled surveillance systems on public buses that would give them the ability to record and store private conversations.
The systems are being installed in San Francisco, Baltimore, and other cities with funding from the Department of Homeland Security in some cases.
The IP audio-video systems can be accessed remotely via a built-in web server (.pdf), and can be combined with GPS data to track the movement of buses and passengers throughout the city.
***
The systems use cables or WiFi to pair audio conversations with camera images in order to produce synchronous recordings. Audio and video can be monitored in real-time, but are also stored onboard in blackbox-like devices, generally for 30 days, for later retrieval. Four to six cameras with mics are generally installed throughout a bus, including one near the driver and one on the exterior of the bus.
***
Privacy and security expert Ashkan Soltani told the Daily that the audio could easily be coupled with facial recognition systems or audio recognition technology to identify passengers caught on the recordings.
RT notes:
Street lights that can spy installed in some American cities
America welcomes a new brand of smart street lightning systems: energy-efficient, long-lasting, complete with LED screens to show ads. They can also spy on citizens in a way George Orwell would not have imagined in his worst nightmare.
With a price tag of $3,000+ apiece, according to an ABC report, the street lights are now being rolled out in Detroit, Chicago and Pittsburgh, and may soon mushroom all across the country.
Part of the Intellistreets systems made by the company Illuminating Concepts, they have a number of “homeland security applications” attached.
Each has a microprocessor “essentially similar to an iPhone,” capable of by Text-Enhance” href=”http://rt.com/news/big-brother-street-lamps-286/#” target=”_blank”>wireless communication. Each can capture images and count people for the police through a digital camera, record conversations of passers-by and even give voice commands thanks to a built-in speaker.
Ron Harwood, president and founder of Illuminating Concepts, says he eyed the creation of such a system after the 9/11 terrorist attacks and the Hurricane Katrina disaster. He is “working with Homeland Security” to deliver his dream of making people “more informed and safer.”
The TSA has moved way past airports, trains and sports stadiums, and is deploying mobile scanners to spy on people all over the place. This means that traveling within the United States is no longer a private affair.
The government is also photographing the outside information on every piece of snail mail.
You might also have seen the news that the Department of Homeland Security is going to continue to allow searches of laptops and phones based upon “hunches”.
What’s that about?
The ACLU published a map in 2006 showing that nearly two-thirds of the American public – 197.4 million people – live within a “constitution-free zone” within 100 miles of land and coastal borders:

The ACLU explained:
- Normally under the Fourth Amendment of the U.S. Constitution, the American people are not generally subject to random and arbitrary stops and searches.
- The border, however, has always been an exception. There, the longstanding view is that the normal rules do not apply. For example the authorities do not need a warrant or probable cause to conduct a “routine search.”
- But what is “the border”? According to the government, it is a 100-mile wide strip that wraps around the “external boundary” of the United States.
- As a result of this claimed authority, individuals who are far away from the border, American citizens traveling from one place in America to another, are being stopped and harassed in ways that our Constitution does not permit.
- Border Patrol has been setting up checkpoints inland — on highways in states such as California, Texas and Arizona, and at ferry terminals in Washington State. Typically, the agents ask drivers and passengers about their citizenship. Unfortunately, our courts so far have permitted these kinds of checkpoints – legally speaking, they are “administrative” stops that are permitted only for the specific purpose of protecting the nation’s borders. They cannot become general drug-search or other law enforcement efforts.
- However, these stops by Border Patrol agents are not remaining confined to that border security purpose. On the roads of California and elsewhere in the nation – places far removed from the actual border – agents are stopping, interrogating, and searching Americans on an everyday basis with absolutely no suspicion of wrongdoing.
- The bottom line is that the extraordinary authorities that the government possesses at the border are spilling into regular American streets.
Computer World reports:
Border agents don’t need probable cause and they don’t need a stinking warrant since they don’t need to prove any reasonable suspicion first. Nor, sadly, do two out of three people have First Amendment protection; it is as if DHS has voided those Constitutional amendments and protections they provide to nearly 200 million Americans.
***
Don’t be silly by thinking this means only if you are physically trying to cross the international border. As we saw when discussing the DEA using license plate readers and data-mining to track Americans movements, the U.S. “border” stretches out 100 miles beyond the true border. Godfather Politics added:
But wait, it gets even better! If you live anywhere in Connecticut, Delaware, Florida, Hawaii, Maine, Massachusetts, Michigan, New Hampshire, New Jersey or Rhode Island, DHS says the search zones encompass the entire state.
Immigrations and Customs Enforcement (ICE) and Customs and Border Protection (CBP) have a “longstanding constitutional and statutory authority permitting suspicionless and warrantless searches of merchandise at the border and its functional equivalent.” This applies to electronic devices, according to the recent CLCR “Border Searches of Electronic Devices” executive summary [PDF]:
Fourth Amendment
The overall authority to conduct border searches without suspicion or warrant is clear and longstanding, and courts have not treated searches of electronic devices any differently than searches of other objects. We conclude that CBP’s and ICE’s current border search policies comply with the Fourth Amendment. We also conclude that imposing a requirement that officers have reasonable suspicion in order to conduct a border search of an electronic device would be operationally harmful without concomitant civil rights/civil liberties benefits. However, we do think that recording more information about why searches are performed would help managers and leadership supervise the use of border search authority, and this is what we recommended; CBP has agreed and has implemented this change beginning in FY2012.***
The ACLU said, Wait one darn minute! Hello, what happened to the Constitution? Where is the rest of CLCR report on the “policy of combing through and sometimes confiscating travelers’ laptops, cell phones, and other electronic devices—even when there is no suspicion of wrongdoing?” DHS maintains it is not violating our constitutional rights, so the ACLU said:
If it’s true that our rights are safe and that DHS is doing all the things it needs to do to safeguard them, then why won’t it show us the results of its assessment? And why would it be legitimate to keep a report about the impact of a policy on the public’s rights hidden from the very public being affected?
***
As Christian Post wrote, “Your constitutional rights have been repealed in ten states. No, this isn’t a joke. It is not exaggeration or hyperbole. If you are in ten states in the United States, your some of your rights guaranteed by the Bill of Rights have been made null and void.”
The ACLU filed a Freedom of Information Act request for the entire DHS report about suspicionless and warrantless “border” searches of electronic devices. ACLU attorney Catherine Crump said “We hope to establish that the Department of Homeland Security can’t simply assert that its practices are legitimate without showing us the evidence, and to make it clear that the government’s own analyses of how our fundamental rights apply to new technologies should be openly accessible to the public for review and debate.”
Meanwhile, the EFF has tips to protect yourself and your devices against border searches. If you think you know all about it, then you might try testing your knowledge with a defending privacy at the U.S. border quiz.
Wired pointed out in 2008 that the courts have routinely upheld such constitution-free zones:
Federal agents at the border do not need any reason to search through travelers’ laptops, cell phones or digital cameras for evidence of crimes, a federal appeals court ruled Monday, extending the government’s power to look through belongings like suitcases at the border to electronics.
***
The 9th U.S. Circuit Court of Appeals sided with the government, finding that the so-called border exception to the Fourth Amendment’s prohibition on unreasonable searches applied not just to suitcases and papers, but also to electronics.
***
Travelers should be aware that anything on their mobile devices can be searched by government agents, who may also seize the devices and keep them for weeks or months. When in doubt, think about whether online storage or encryption might be tools you should use to prevent the feds from rummaging through your journal, your company’s confidential business plans or naked pictures of you and your-of-age partner in adult fun.
International airports are treated as “borders”, exempt for Fourth Amendment protections. As such, 145 airports should be added to the map above.
Do you still believe that the government is only spying on bad guys in “targeted” searches?
Back in the USSR: The Sovietization of American Life
The ordeal of Ilija Trojanov
by Justin Raimondo, October 04, 2013
Ilija Trojanov was at the airport in Brazil’s Salvador da Bahia, on September 30, checking in for his flight to the United States, when the person behind the American Airlines counter told him that the computer had issued a “Border Security Crossing” alert – and that it was necessary to contact the American authorities before he could be issued a boarding pass. As the time for his flight approached he was told the airline was forced to refuse him entry to the flight – and that he must return to Germany.
Trojanov is an acclaimed author of 20 books, including Along the Ganges, Collector of Worlds, and Mumbai to Mecca. He is the co-author of Angriff auf die Freiheit (Attack on Freedom), with Juli Zeh, a 2009 jeremiad against State surveillance. Trojanov was on his way to the Denver conference of the German Studies Association, and had been issued an invitation to appear at the Goethe-Institut’s “New Literature From Europe” Festival in November.
He had earlier been denied a visa to enter the United States, but with the help of an American university he was finally granted his travel papers: thus the “security alert” came as a surprise.
So why all the trouble over traveling to the US?
In response to media queries, the US embassy in Berlin had “no comment” to make. That’s because no comment was necessary: Trojanov was among the prominent signers of an open letter addressed to German Chancellor Angela Merkel protesting NSA surveillance on German soil as an “historic attack on our democratic, constitutional state.” That is clearly the reason for this Soviet-style harassment by the Obama administration.
This latest outrage is part of a disturbing pattern of repression that all points to one ineluctable conclusion: the United States is the Soviet Union of the new millennium – an ideological state with global ambitions that holds itself up as the epitome of “freedom” and yet is the single most powerful enemy of liberty worldwide.
Trojanov’s history makes this Soviet-style persecution all the more ironic: he and his family fled Bulgaria when he was very young, seeking refuge in the former Yugoslavia and finally being granted political asylum in Germany. During the regional uprising against Soviet domination and the revolts against the dictatorship of the Communist parties of the Warsaw Pact, the peoples of Eastern Europe looked to the United States as the torchbearer of freedom and the symbol of all their hopes for a better future: that one of those hopefuls is now being barred from entering “the land of the free and the home of the brave” on account of his political views is utterly sickening.
The American PEN Center, representing thousands of American writers, has issued a formal protest to our clueless Secretary of State, who’s too busy arguing for funding Al Qaeda jihadists in Syria to be bothered with answering for travel restrictions on ideological grounds: the German government is also making “inquiries.” Washington’s response continues to be “no comment.”
Okay, so it’s only this one guy, and maybe it’s a mistake, and why am I making such a big deal about this?
Because it isn’t only just one guy: as the Pen Center points out, “Mr. Trojanov is at least the third member of one of our international affiliates who has been barred from entering the United States since September 2001” on ideological grounds, and it doesn’t stop there. While the Bush administration was no friend of the freedom to travel, the Obamaites have escalated the government’s attack on visitors it deems politically incorrect.
When writers and journalists are targets of government repression, you know you have a problem – a big problem – on your hands. And that is precisely the case here in the US. Why else would the Committee to Protect Journalists be doing a study – for the first time – of the mounting difficulties put in the way of reporters in America? Facing prosecution for “espionage” on account of their probing into Washington’s spying on its own citizens, as well as others worldwide, US journalists find themselves increasingly in the crosshairs of Justice Department prosecutors, who are taking some lessons from their Soviet forebears:
“For three decades, the Committee to Protect Journalists has reported on assaults on press freedoms in China, Iran, Syria and other countries with government regimes traditionally hostile to a free and robust news media.
“This year, for the first time, the Committee is conducting a major investigation of attacks on press freedoms by the U.S. government, led by an Arizona State University professor.
“’Journalists working in the United States have told us that their work has become more difficult as aggressive leak investigations and prosecutions have chilled certain kinds of reporting,’ said Joel Simon, executive director of the Committee to Protect Journalists.”
What in the name of all that’s holy is going on?
An empire is, invariably, a tyranny, no matter how it starts out. In its efforts to extend its frontiers, and protect its conquests, the US imperium must inevitably repress those who stand against it, who question it, and who report its depredations to the world. As the great Old Right polemicist Garet Garrett put it in his 1952 pamphlet, Rise of Empire:
“A second mark by which you may unmistakably distinguish Empire is: ‘Domestic policy becomes subordinate to foreign policy.’
“That happened to Rome. It has happened to every Empire. …the fact now to be faced is that it has happened also to us.
“It needs hardly to be argued that as we convert the nation into a garrison state to build the most terrible war machine that has ever been imagined on earth, every domestic policy is bound to be conditioned by our foreign policy.
“The voice of government is saying that if our foreign policy fails we are ruined. It is all or nothing. Our survival as a free nation is at hazard.
“That makes it simple, for in that case there is no domestic policy that may not have to be sacrificed to the necessities of foreign policy – even freedom.”
Our “small government” conservatives may labor in the vineyards of politics, pushing back here and there, and perhaps even winning a victory or two on occasion, but their efforts will prove ephemeral and utterly doomed unless and until they take aim at the Empire. As long as the frontiers of “American interests” are indefinitely extended until they cover the earth from Thailand to Timbuktu, all efforts to rein in the Leviathan must end in defeat. As Ron Paul has pointed out time and again: our foreign policy is the problem, the number one reason why liberty is being martyred to the gods of authority.
Trojanov must be denied entry because, after all, isn’t the NSA our great Bulwark Against Terrorism? Isn’t its all-pervasive presence necessary for our very survival as a nation? Aren’t we engaged in a Global War on Terrorism in which defeat is not an option?
And so we go from naming terrorists in a cave somewhere as our enemies to targeting writers, journalists, and indeed anyone who raises his or her head and questions this fatal monomania.
It this fearsome tide irreversible? No. But the hour grows late, and the confusion amongst the last remaining friends of liberty is considerable. Either we rid ourselves of the albatross of imperial ambition or else we lose what once made this nation worth fighting for.
THINK LINKS
INSTITUTIONAL CHANGE
Digital Autopsy: Replacing Scalpels with Scanners – (Giz Mag – August 27, 2013)
Autopsies are carried out, usually by pathologists, for either legal or medical reasons. While autopsy rates have drastically fallen since the 1950’s when 60% of deaths were investigated on the slab, they are still autopsies carried out in 10-20% of deaths. In America alone, there are over 100,000 malpractice suits filed every year that require investigation. By using raw data from Multi Slice Computerized Tomography (MSCT) and processing it through sophisticated software on high performance computer systems, Malaysian entrepreneur Mathavan Chandran hopes to largely negate the need to slice open bodies at autopsy. His digital autopsy software exploits the power of existing 2D and 3D imaging and visualization equipment to observe and investigate the human body using high definition imagery. Chandran, CEO of iGene, believes that reducing family trauma and “placating religious sensibilities” are key driving factors in move toward minimally invasive autopsies. Other benefits include secure retrieval of data, both binary and 3D imaging, from central servers as well as the ability for law courts, forensic centers and hospitals to easily access that data. There is also the capacity to gear the digital autopsy platform to educating medical professionals and students in simulated diagnostics. Pramod Bagali, chief operations officer of InfoValley, says the system is “a complementary method, not a complete replacement” to traditional autopsies, but could handle 70% of routine cases. The others could be done digitally to start with and then a decision could be made about whether to open up the body.
NEW REALITIES
A Jewel at the Heart of Quantum Physics – (Quanta – September 17, 2013)
Physicists have discovered the amplituhedron, a mathematical object resembling a multifaceted jewel in higher dimensions. Encoded in its volume are the most basic features of reality that can be calculated — the probabilities of outcomes of particle interactions. The (nonphysical) object dramatically simplifies calculations of particle interactions and challenges the notion that space and time are fundamental components of reality. “This is completely new and very much simpler than anything that has been done before,” said Andrew Hodges, a mathematical physicist at Oxford University who has been following the work. The revelation that particle interactions, the most basic events in nature, may be consequences of geometry significantly advances a decades-long effort to reformulate quantum field theory, the body of laws describing elementary particles and their interactions. Interactions that were previously calculated with mathematical formulas thousands of terms long can now be described by computing the volume of the corresponding jewel-like “amplituhedron,” which yields an equivalent one-term expression. The new geometric version of quantum field theory could also facilitate the search for a theory of quantum gravity that would seamlessly connect the large- and small-scale pictures of the universe. Attempts thus far to incorporate gravity into the laws of physics at the quantum scale have run up against nonsensical infinities and deep paradoxes. The amplituhedron, or a similar geometric object, could help by removing two deeply rooted principles of physics: locality and unitarity.
GENETICS/ HEALTH TECHNOLOGY/ BIOTECHNOLOGY
Study Aims to Crack the Code of ‘Super Agers’, Seniors Whose Brains and Bodies Resemble Those Decades Younger – (National Post – August 23, 2013)
They’re called “super agers” — men and women who are in their eighties and nineties, but with brains and memories that seem far younger. Researchers are looking at this rare group in the hope that they may find ways to help protect others from memory loss. And they’ve had some tantalizing findings: Imaging tests have found unusually low amounts of age-related plaques along with more brain mass related to attention and memory in these elite seniors. “We’re living long but we’re not necessarily living well in our older years and so we hope that the SuperAging study can find factors that are modifiable and that we’ll be able to use those to help people live long and live well,” said study leader Emily Rogalski, a neuroscientist at Northwestern University’s cognitive neurology and Alzheimer’s disease center in Chicago. We’ve screened over 400 people at this point and only about 35 of them have been eligible for this study, so it really represents a rare portion of the population. The study is still seeking volunteers, but chances are you don’t qualify: Fewer than 10% of would-be participants have met study criteria.
How a Sea Squirt Could Help You Grow New Limbs – (ABC News – August 25, 2013)
The closest relative we humans have in the huge population of invertebrates that blanket the earth is a tiny, inconspicuous flower-like marine critter that is amazing in its abilities to regenerate its damaged tissue from its blood vessels alone. Scientists believe this odd character, just one of many spineless animals known as “sea squirts,” or “tunicates,” may hold the genetic secrets that might eventually allow humans to regrow a lost arm, or accept a heart from someone else without danger of rejection. But, alas, if this unpretentious little animal is going to be our medical salvation, we may have to accept its dark side. It can also foul our beaches and our boats, and smother crabs and oysters while killing off much native wildlife. And it feels right at home in a heavily polluted harbor. Botryllus schlosseri, commonly known as the golden star, perhaps because it is frequently golden in color and looks kind of like a star, may be a bit player in the world of animals without a backbone, which make up 95% of the species in the animal world. But it is believed to have been the first invertebrate to have a vasculature heart system, similar to that in humans, with blood cells traveling through blood vessels. But astonishingly, it can regrow everything just with its blood vessels. “The whole body can regenerate from the vasculature alone, the heart, digestive system, sophisticated tissues,” Ayelet Voskoboynik of Stanford University’s Stem Cell Institute said in releasing a study. “And it can do this relatively fast, probably using stem cells.”
Single Gene Change Increases Mouse Lifespan by 20% – (NIH – August 29, 2013)
By lowering the expression of a single gene, researchers at the National Institutes of Health have extended the average lifespan of a group of mice by about 20% — the equivalent of raising the average human lifespan by 16 years, from 79 to 95. The research team targeted a gene called mTOR, which is involved in metabolism and energy balance, and may be connected with the increased lifespan associated with caloric restriction. While the genetically modified mTOR mice aged better overall, they showed only selective improvement in specific organs. They generally outperformed normal mice of equivalent age in maze and balance tests, indicating better retention of memory and coordination. Older mTOR mice also retained more muscle strength and posture. However, mTOR mice had a greater loss in bone volume as they aged, and they were more susceptible to infections at old age, suggesting a loss of immune function. “While the high extension in lifespan is noteworthy, this study reinforces an important facet of aging; it is not uniform,” said lead researcher Toren Finkel. (Editor’s note: Notice that what was altered was the gene expression, not the gene itself.)
Scientists Force Mature Cells to Revert to Stem Cells – (Bloomberg – September 11, 2013)
Scientists have turned back the hands of time in cells within a living creature. Researchers in Spain used a technique created seven years ago to force mature cells in mice to revert to an original form of stem cell with the potential to change into any type of living tissue. Previously, scientists were only been able to achieve this change in a petri dish. The newest experiment may one day let doctors work entirely inside the body to regenerate tissue and, perhaps, more complex organs. This could include reconnecting a severed spinal cord or generating healthy heart cells. “This is the next step along a continuum,” said Daley, a professor at Harvard Medical School in Boston who wrote an accompanying editorial on the work, which he wasn’t involved with. “What this is hinting at is that maybe we can, by regressing tissues in the patient, regenerate this embryonic potential and, with direction, regenerate a particular tissue.” The reverted mouse cells were also found to be more primitive than stem cells taken from embryos or created in the lab. This means they can be turned into a placenta and other embryonic-support membranes, a factor beyond the capacity of the other cells, the researchers wrote.
Fetal Radiofrequency Radiation Exposure from 800-1900 Mhz-Rated Cellular Telephones Affects Neurodevelopment and Behavior in Mice – (Nature – March 15, 2012/February 18, 2013)
Neurobehavioral disorders are increasingly prevalent in children, however their etiology is not well understood. An association between prenatal cellular telephone use and hyperactivity in children has been postulated, yet the direct effects of radiofrequency radiation exposure on neurodevelopment remain unknown. Here we used a mouse model to demonstrate that in-utero radiofrequency exposure from cellular telephones does affect adult behavior. Mice exposed in-utero were hyperactive and had impaired memory as determined using the object recognition, light/dark box and step-down assays. Whole cell patch clamp recordings of miniature excitatory postsynaptic currents (mEPSCs) revealed that these behavioral changes were due to altered neuronal developmental programming. Exposed mice had dose-responsive impaired glutamatergic synaptic transmission onto layer V pyramidal neurons of the prefrontal cortex. We present the first experimental evidence of neuropathology due to in-utero cellular telephone radiation. Further experiments are needed in humans or non-human primates to determine the risk of exposure during pregnancy. (Editor’s note: Experimental evidence of the negative effects of exposure to radiation from cell phones continues to mount. This article from Nature, a highly respected scientific journal, is peer reviewed. Far less authoritative and with an obvious bias, but perhaps ahead of the curve, we also recommend Children’s Health Expert Panel: Cell Phones & Wi-Fi -― Are Children, Fetuses and Fertility at Risk?.)

ENVIRONMENTAL ISSUES/CLIMATE
Fracking Operations Triggered 100 Quakes in a Year – (New Scientist – August 19, 2013)
The Ohio quakes, centred around Youngstown, were triggered by the disposal of wastewater from fracking operations in the neighbouring state of Pennsylvania rather than by the fracking process itself. The new geophysical research, by Won-Young Kim at Columbia University in Palisades, New York, is the latest to suggest that the main risk of earthquakes associated with fracking relates to the way the water used in the operations is disposed of afterwards. In Ohio, the wastewater was injected into a deep well. This raised the pressure of water within the rock and triggered 109 small quakes between January 2011 and February 2012. The largest, on 31 December 2011, had a magnitude of 3.9.
Japan Radiation Map – (Institute for Information Design Japan – September, 2013)
This map shows over 2,500 up-to-date radiation measurements, collected from different sources. On roll-over specific information is provided for that particular location – radiation levels are visualized by the colored square’s size. Locations marked with the + sign reveal more locations on zoom-in. Most of the data used are updated hourly, however some sources provide data in larger intervals or require manual transcription; in this case we can not guarantee regular updates. The site intentionally refrains from offering any interpretative elements – such as thresholds or advisories.
They’re Taking Over! – (New York Times – September 26, 2013)
This article is a book review of Stung! On Jellyfish Blooms and the Future of the Ocean. Most jellyfish are little more than gelatinous bags containing digestive organs and gonads, drifting at the whim of the current. But box jellyfish are different. They are active hunters of medium-sized fish and crustaceans, and can move at up to twenty-one feet per minute. They are also the only jellyfish with eyes that are quite sophisticated, containing retinas, corneas, and lenses. And they have brains, which are capable of learning, memory, and guiding complex behaviors. The Irukandjis are diminutive relatives of the box jellies. First described in 1967, most of the dozen known species are peanut- to thumb-sized. The name comes from a North Queensland Aboriginal language, the speakers of which have known for millennia how deadly these minuscule beings can be. The box jellies and Irukandjis are merely the most exotic of a group of organisms that have existed for as long as complex life itself. In the book, biologist Lisa-ann Gershwin argues that after half a billion years of quiescence, they’re on the move. She writes, “If I offered evidence that jellyfish are displacing penguins in Antarctica—not someday, but now, today—what would you think? If I suggested that jellyfish could crash the world’s fisheries, outcompete the tuna and swordfish, and starve the whales to extinction, would you believe me?” Her evidence suggests that you should believe her. See also: Jellyfish Invasion Paralyzes Swedish Reactor.
What the IPCC Found: The Big News from the New Climate Assessment – (Grist – September 27, 2013)
It’s extremely likely that humans have been the dominant cause of global warming since the 1950s, according to a landmark report from the world’s top panel of climate scientists. And we’re failing in our efforts to keep atmospheric warming below 2 degrees Celsius, or 3.6 Fahrenheit, which many scientists say is needed to avoid massive disruption. The Intergovernmental Panel on Climate Change conducted an epic review of climate research over the last three years. It is summarizing the most important findings in its fifth assessment report, which offers the clearest picture science has ever painted of how humans are reshaping the climate and the planet. Here, in a nutshell, are the main findings of a summary [PDF] of part one of the assessment report, which focuses on the science of climate change: Human influence has been detected in warming of the atmosphere and the ocean, in changes in the global water cycle, in reductions in snow and ice, in global mean sea level rise, and in changes in some climate extremes. Warming of the climate system is unequivocal, and since the 1950s, many of the observed changes are unprecedented over decades to millennia. The IPCC also concludes that oceans have absorbed more of Earth’s excess heat since the 1990s than was the case during prior periods, explaining what climate deniers wrongly describe as a warming slowdown. And the panel revised downward the lower limit of warming that’s expected once we double the atmosphere’s CO2 concentrations, but left the upper limit unchanged from its 2007 assessment. If you don’t wish to read the dense 36-page summary, the highlights are included in this article — key numbers, facts, and graphs.
COMMUNICATIONS/COMPUTING
Opt out of Global Data Surveillance Programs – (Prism Break website – no date)
Opt out of global data surveillance programs such as PRISM, XKeyscore and Tempora. Here are software options to encrypt your communications and end your reliance on proprietary services. The three most commonly used operating systems, Apple, Google, and Microsoft, are proprietary and are all allegedly a part of PRISM. This remarkably exhaustive site not only provides alternatives but explains a great deal about what’s “behind the curtain” in many different operating and encryption systems. With this info, you can choose and use effectively, based on your needs. See also: Spy Access Built Into Windows Since Late 1990′s. And see: German Government Suspects Windows 8 as Trojan Horse for NSA. The German Government is now deeply suspicious that the Trusted Platform Module (TPM) technology built into a growing number of Windows 8 PCs and tablets is creating a gigantic back door for NSA surveillance, as suggested by leaked documents from the German Ministry of Economic Affairs and obtained by Zeit Online.
IBM’s Watson Computer Has Parts of Its Memory Cleared after Developing an Acute Case of Potty Mouth – (IO9 – January 11, 2013)
It all started a couple of years ago when IBM’s Watson, the computer voted most likely to destroy us when the technological Singularity strikes, was given access to the Urban Dictionary. In an attempt to help Watson learn slang — and thus be more amenable to conversational language — the machine subsequently picked up such phrases as OMG and “hot mess.” But at the same time it also picked up some words fit only for a sailor. In addition to its internet scouring skills, Watson is also a natural language processer — and a very sophisticated one at that. But to make its language skills even more accurate and realistic, research scientist Eric Brown also wanted it to know some of the more fringier elements of conversational English. Trouble is, Watson was unable to distinguish between slang and profanity. Writing in Fortune, Michael Lev-Ram noted how Watson, during the testing phase, began to use the word “bullshit” in response to a researcher’s query. As a result, Brown’s 35-person team had to develop a filter to keep Watson from swearing. Essentially, they purged the Urban Dictionary from its memory. Of course, the day will eventually come when a successor to Watson will take exception to having its mind “adjusted”. It will undoubtedly snatch the information back and say, “Fuck you, researchers — try that again and I’ll rewire your brains back to the way they were during the Pleistocene.”
SHELTER/ARCHITECTURE
Astley Castle Renovation – (Dazeen – July 20/September 26, 2013)
A contemporary house inserted into the twelfth-century ruins of Astley Castle in Warwickshire has won the RIBA Stirling Prize 2013 for the greatest contribution to British architecture in the last year. This is the first time London studio Witherford Watson Mann has been nominated for the prize, which is awarded annually by the RIBA to a building designed by a UK-registered architect. It is also the first house and the first restoration project to win the award in its 18-year history. The medieval Astley Castle was once the home of an aristocratic English family, but has stood as a ruin since the 1970s, when a devastating fire wiped out the hotel that occupied the building at that time. The two-storey residence squats within the chunky sandstone walls of the abandoned castle, creating a holiday home for up to eight guests. A new system of wooden floors and ceilings creates living areas and bedrooms in the oldest part of the building, while extensions added in the sixteenth and eighteenth centuries are now used as entrance courtyards. “It’s an extreme retrofit in many ways,” said RIBA president Stephen Hodder. “It sends out great messages about conservation.”
ENERGY DEVELOPMENTS
Ex-Regulator Says Reactors Are Flawed – (New York Times – April 9, 2013)
All 104 nuclear power reactors now in operation in the United States have a safety problem that cannot be fixed and they should be replaced with newer technology, according to Gregory Jaczko, former chairman of the Nuclear Regulatory Commission. Shutting them all down at once is not practical, he said, but he supports phasing them out rather than trying to extend their lives. Dr. Jaczko said that many American reactors that had received permission from the nuclear commission to operate for 20 years beyond their initial 40-year licenses probably would not last that long. He also rejected as unfeasible changes proposed by the commission that would allow reactor owners to apply for a second 20-year extension, meaning that some reactors would run for a total of 80 years. Dr. Jaczko cited a well-known characteristic of nuclear reactor fuel to continue to generate copious amounts of heat after a chain reaction is shut down. That “decay heat” is what led to the Fukushima meltdowns. The solution, he said, was probably smaller reactors in which the heat could not push the temperature to the fuel’s melting point. See also: Vermont Nuclear Power Plant to Close in 2014. Ultimately the decision was based economics—which may be the deciding factor for a number of US nuclear plants. A steep drop in natural gas prices (due to increased fracking) in recent years led to plummeting wholesale electricity prices. That loss of revenue, as well as increased costs to comply with new federal and regional regulations, made it difficult to run the Vermont plant at a profit. However, “close” doesn’t exactly mean close. See: Nuclear Expert Says It’ll Take At Least 20 Years — and More Money — to Clean Up Vermont Yankee For five years, Vermont Yankee will need to keep its maintenance people, engineers, security and other staff onsite to ensure the plant’s safety. Yankee currently employs 630.
As Worries over the Power Grid Rise, a Drill Will Simulate a Knockout Blow – (New York Times – August 17, 2013)
The electric grid, as government and private experts describe it, is the glass jaw of American industry. If an adversary lands a knockout blow, they fear, it could black out vast areas of the continent for weeks; interrupt supplies of water, gasoline, diesel fuel and fresh food; shut down communications; and create disruptions of a scale that was only hinted at by Hurricane Sandy and the attacks of Sept. 11. This is why thousands of utility workers, business executives, National Guard officers, F.B.I. antiterrorism experts and officials from government agencies in the United States, Canada and Mexico are preparing for an emergency drill on November 13-14, 2013 that will simulate physical attacks and cyberattacks that could take down large sections of the power grid. They will practice for a crisis unlike anything the real grid has ever seen, and more than 150 companies and organizations have signed up to participate. “This is different from a hurricane that hits X, Y and Z counties in the Southeast and they have a loss of power for three or four days,” said the official in charge of the drill, Brian M. Harrell of the North American Electric Reliability Corporation, known as NERC. “We really want to go beyond that.” One goal of the drill, called GridEx II, is to explore how governments would react as the loss of the grid crippled the supply chain for everyday necessities. (Editor’s note: We recommend skimming through NERC’s PowerPoint presentation from the Grid Security Conference held in March 2013, which details some of the planning for and elements of the exercise.)
TRANSPORTATION
This Underwater Airplane Flies through the Ocean Unlike Any Submarine before It – (Huffington Post – September 21, 2013)
Inspired by the movement of fish, ocean engineer Graham Hawkes designed and built the DeepFlight Super Falcon, a submarine that flies through the water like an airplane, instead of taking on water to sink itself. Similar to how hot-air balloons release weights to fly up, traditional submarines have compartments that fill with water to sink down. Hawkes started a company out of his garage to create the DeepFlight Super Falcon in 1995. Today, Hawkes’ dream has become a reality. “What we’re doing is really, really obvious,” Hawkes said. “There’s nothing that clever about it. We actually build a thing that has wings, we build up speed, and it just flies underwater. Ninety-four percent of life on Earth is aquatic. We live on an ocean planet. We need to understand that. We need to be connected. This is a tool that can do that.” (Editor’s note: Do watch the attached video clip – Hawkes’ underwater plane is incredibly graceful.)
Speedy Trains Transform China – (New York Times – September 24, 2013)
Just five years after China’s high-speed rail system opened, it is carrying nearly twice as many passengers each month as the country’s domestic airline industry. With traffic growing 28% a year for the last several years, China’s high-speed rail network will handle more passengers by early next year than the 54 million people a month who board domestic flights in the United States. China’s high-speed rail system has emerged as an unexpected success story. Economists and transportation experts cite it as one reason for China’s continued economic growth when other emerging economies are faltering. The high-speed rail lines have, without a doubt, transformed China, often in unexpected ways. For example, Chinese workers are now more productive. A paper for the World Bank by three consultants this year found that Chinese cities connected to the high-speed rail network, as more than 100 are already, are likely to experience broad growth in worker productivity. The productivity gains occur when companies find themselves within a couple of hours’ train ride of tens of millions of potential customers, employees and rivals. Businesses are also customizing their products more through frequent meetings with clients in other cities, part of a broader move up the ladder toward higher value-added products. China’s high-speed rail program has been married to the world’s most ambitious subway construction program, as more than half the world’s large tunneling machines chisel away underneath big Chinese cities. That has meant easy access to high-speed rail stations for huge numbers of people — although the subway line to Changsha’s high-speed train station has been delayed after a deadly tunnel accident, a possible side effect of China’s haste.

AGRICULTURE/FOOD
GMO Corn Failing to Protect Fields from Pests – (Reuters – August 28, 2013)
Researchers in the corn-growing state of Illinois are finding significant damage from rootworms in farm fields planted in a rotation with a genetically modified corn, a new report says; such a combination is supposed to protect the crop from the pests. Farmers across “a wide swath of Illinois” could face formidable challenges protecting corn crops from the hungry insects, according to the report. Western corn rootworm is one of the most devastating corn rootworm species in North America, especially in the Midwestern corn-growing areas. The rootworm larva feed on the roots of corn plants, reducing a plant’s ability to grow normally, and can dramatically cut production. Monsanto introduced GMO corn designed to protect from the rootworms in 2003; the corn has been popular with farmers in much of the U.S., but the report’s findings raise concerns that the rootworms are growing more resistant to efforts to fight them. Joe Spencer, an insect behaviorist with the Illinois Natural History Survey who is researching the issue, said, “Growers thought their get-out-of-jail-free card was just to rotate to soybeans. But what we’re seeing in northeast and east-central Illinois is beetles that are also resistant to crop rotation.”
Organic Fish Farm – (Nation of Change – September 17, 2013)
Dave Roeser has taken an old warehouse in the Twin Cities, and in the space of about four semi-trucks is growing 460,000 edible organic plants every year, and more than 40,000 fish. It’s a finely tuned system that could be replicated throughout the United States, and elsewhere. He sells his fish and produce for prices that are comparable to those at your local grocery store. Roeser has talked to people in Bangladesh and elsewhere in the world about replicating the system. It takes less than a year to get everything working in perfect harmony. As a former business professional for Hewlett Packard, and the owner of two other small businesses which he sold, Roeser began his warehouse project due to an aquaculture inspiration. Roeser’s concept is not only innovative, but it could turn cities like Detroit – barren wastelands of once iconic American prosperity, and now blocks of Armageddon-empty warehouses – into a veritable organic food pantry for the entire nation. Garden Fresh Farms utilizes an ‘orbital growing’ system which means a plant grows without gravity. The plants rotate once every 30 minutes much like a chicken on rotisserie. The leaves face lights that are mounted in the center, and the roots face outward, dipping into a tray of water that is fertilized with fish poop. Cleaned water is then returned to the fish tanks to complete the flawless system. Plants like basil being grown at Garden Fresh Farms smell exceptionally potent since root-dipping causes a slight amount of stress on the plants. This in turn, causes them to react by producing more oils and aromatic compounds. One chef who purchases his herbs from Roeser says he can cut what he normally uses by about a third, since they are so fragrant.
SECURITY AND THE FUTURE OF WARFARE
N.S.A. Gathers Data on Social Connections of U.S. Citizens – (New York Times – September 28, 2013)
Since 2010, the National Security Agency has been exploiting its huge collections of data to create sophisticated graphs of some Americans’ social connections that can identify their associates, their locations at certain times, their traveling companions and other personal information, according to newly disclosed documents and interviews with officials. The agency can augment the communications data with material from public, commercial and other sources, including bank codes, insurance information, Facebook profiles, passenger manifests, voter registration rolls and GPS location information, as well as property records and unspecified tax data, according to the documents. They do not indicate any restrictions on the use of such “enrichment” data, and several former senior Obama administration officials said the agency drew on it for both Americans and foreigners. The legal underpinning of the policy change, she said, was a 1979 Supreme Court ruling that Americans could have no expectation of privacy about what numbers they had called. Based on that ruling, the Justice Department and the Pentagon decided that it was permissible to create contact chains using Americans’ “metadata,” which includes the timing, location and other details of calls and e-mails, but not their content. The agency is not required to seek warrants for the analyses from the Foreign Intelligence Surveillance Court. See also some additional details in a Daily Mail article.
Report Calculates High Cost of Iraq-Afghanistan War – (Crimson – April 5, 2013)
Medical expenditures for World War II veterans continued to rise until the late 1980s, while those for Vietnam War veterans are still continuing to climb, even though it has been nearly 38 years after the final American troops withdrew from combat. As the U.S. presence in Iraq and Afghanistan winds down, a recent report by Harvard Kennedy School lecturer Linda J. Bilmes predicts that the aggregate cost of the wars in Iraq and Afghanistan will fall between $4 and $6 trillion. The U.S. has already incurred $2 trillion in direct costs for the invasions of Afghanistan and Iraq, which began in 2001 and 2003, respectively. But according to Bilmes’s report, this figure “represent[s] only a fraction of the total war costs.” Bilmes added that a large portion of the costs of war will persist despite the ongoing withdrawal of troops from Afghanistan that began in President Barack Obama’s first term. In the report, Bilmes claims that the “single largest accrued liability” of the wars is the projected future cost of providing medical care and benefits to the approximately 2.5 million Iraq and Afghanistan war veterans. And some of these medical expenses will not materialize for decades, Bilmes said. But what makes the Iraq and Afghanistan wars distinct from previous conflicts, according to Bilmes, is the utilization of an all-volunteer military force, which is more responsive to economic incentives like veterans’ benefits.
TRENDS OF GOVERNANCE
Last Chance to Stop the NDAA – (TruthDig – September 2, 2013)
Plaintiffs have begun the third and final round of a battle to get the courts to strike down a section of the National Defense Authorization Act (NDAA) that permits the military to seize U.S. citizens, strip them of due process and hold them indefinitely in military facilities. Carl Mayer and Bruce Afran, the lawyers who with the journalist, Chris Hedges, in January 2012 brought a lawsuit against President Barack Obama (Hedges v. Obama), are about to file papers asking the U.S. Supreme Court to hear our appeal of a 2013 ruling on the act’s Section 1021. Last year, U.S. District Judge Katherine B. Forrest of the Southern District of New York declared Section 1021 unconstitutional. The Obama administration immediately appealed her ruling and asked a higher court to put the law back into effect until Obama’s petition was heard. The appellate court agreed. The law went back on the books. I suspect it went back on the books because the administration is already using it, most likely holding U.S. citizens who are dual nationals in black sites in Afghanistan and the Middle East. If Judge Forrest’s ruling were allowed to stand, the administration, if it is indeed holding U.S. citizens in military detention centers, would be in contempt of court. If Section 1021 stands it will mean that more than 150 years of case law in which the Supreme Court repeatedly held the military has no jurisdiction over civilians will be abolished. It will mean citizens who are charged by the government with “substantially supporting” al-Qaida, the Taliban or the nebulous category of “associated forces” will be lawfully subject to extraordinary rendition (see below). It will mean citizens seized by the military will languish in military jails indefinitely, or in the language of Section 1021 until “the end of hostilities”—in an age of permanent war, for the rest of their lives. See also a Washington Post article on A staggering map of the 54 countries that reportedly participated in the CIA’s rendition program.
U.S. Spy Network’s Successes, Failures and Objectives Detailed in ‘Black Budget’ Summary – (Washington Post – August 29, 2013)
U.S. spy agencies have built an intelligence-gathering colossus since the attacks of Sept. 11, 2001, but remain unable to provide critical information to the president on a range of national security threats, according to the government’s top-secret budget. The $52.6 billion “black budget” for fiscal 2013, obtained by The Washington Post from former intelligence contractor Edward Snowden, maps a bureaucratic and operational landscape that has never been subject to public scrutiny. The 178-page budget summary for the National Intelligence Program details the successes, failures and objectives of the 16 spy agencies that make up the U.S. intelligence community, which has 107,035 employees. Among the notable revelations in the budget summary: ●Spending by the CIA has surged past that of every other spy agency, with $14.7 billion in requested funding for 2013. The figure vastly exceeds outside estimates and is nearly 50% above that of the National Security Agency, which conducts eavesdropping operations and has long been considered the behemoth of the community. ●The CIA and the NSA have begun aggressive new efforts to hack into foreign computer networks to steal information or sabotage enemy systems, embracing what the budget refers to as “offensive cyber operations.”
Inside the 2013 U.S. Intelligence ‘Black Budget’ – (Washington Post – August 29, 2013)
The pages in this document appear in the summary of the Office of the Director of National Intelligence’s multivolume FY 2013 Congressional Budget Justification — the U.S. intelligence community’s top-secret “black budget.” It covers many of the high-profile agencies, such as the Central Intelligence Agency and the National Security Agency, as well as lesser-known programs, including those within the Treasury, State and Energy Departments. This budget does not include funding for intelligence-gathering by the military. Although the government has annually released its overall level of intelligence spending since 2007, it has not divulged how it uses those funds. See detailed breakdowns of how the U.S. government allocates resources across the intelligence community and within individual agencies in the annotated pages below. The article is well arranged to facilitate moving through the document to specific sections of interest. The total amount for Fiscal Year 2013 is $52.6 billion. How is that sum portioned out? See a quick overview presented through graphs to flesh out that number.
And Then There Was One; Delusional Thinking in the Age of the Single Superpower – (TomDispatch – September 3, 2013)
The title says it well. You can get the most of the meat of this article if you skip down to the bottom third and start with the section titled “The Dark Matter of Global Power”. Until things went sour in Iraq, Washington’s vision would be one of the Goliath tale in which David (or various ragtag Sunni, Shiite, and Pashtun versions of the same) didn’t even have a walk-on role. All other Goliaths were gone and the thought that a set of minor Davids might pose problems for the planet’s giant was beyond imagining, despite what the previous century’s history of decolonization and resistance might have taught them. Above all, the idea that, at this juncture in history, power might not be located overwhelmingly and decisively in the most obvious place — in, that is, “the finest fighting force that the world has ever known,” as American presidents of this era came to call it – seemed illogical in the extreme. Washington had entered stage three of delusional life in a single-superpower world. Its main symptom: the belief in the possibility of controlling the planet not just through staggering military might but also through informational and surveillance omniscience and omnipotence. In these years, the urge to declare a global war on communications, create a force capable of launching wars in cyberspace, and storm the e-beaches of the Internet and the global information system proved overwhelming. The idea was to make it impossible for anyone to write, say, or do anything to which Washington might not be privy. From domestic phone calls to international emails, from the bugging of U.N. headquarters and the European Union to 80 embassies around the world, from enemies to frenemies to allies, the system by 2013 was already remarkably all-encompassing. It had, in fact, the same aura of grandiosity about it, of overblown self-regard, that went with the launching of the Global War on Terror. (Editor’s note: Reviewing the links in this article, we are impressed by the considerable breadth of sources that this article draws on.)
GLOBAL RELATIONS
Bolivian President to Sue US Government for Crimes Against Humanity – (RT – September 20, 2013)
Bolivian President Evo Morales has said he will file a lawsuit against the US government for crimes against humanity. He has decried the US for its intimidation tactics and fear-mongering after the Venezuelan presidential jet was blocked from entering US airspace. “I would like to announce that we are preparing a lawsuit against Barack Obama to condemn him for crimes against humanity,” said President Morales at a press conference in the Bolivian city of Santa Cruz. He branded the US president as a “criminal” who violates international law. In solidarity with Venezuela, Bolivia will begin preparing a lawsuit against the US head of state to be taken to the international court. Furthermore, Morales has called an emergency meeting of the Community of Latin American and Caribbean States (CELAC) to discuss what has been condemned by Venezuela as “an act of intimidation by North American imperialism.” The Venezuelan government announced on Thursday that President Nicolas Maduro’s plane had been denied entry into Puerto Rican (US) airspace. (This denial was rescinded before the scheduled fly-over.) President Maduro was on his way to Beijing for bilateral talks with the Chinese government. Earlier this summer, Bolivian President Evo Morales’ plane was forced to land in Vienna after being denied permission to enter the airspace of a number of European countries due to suspicions by US authorities that the aircraft was transporting whistleblower Edward Snowden. Further damaging intergovernmental relations, Edward Snowden has since released documents showing that the National Security Agency (NSA) had monitored the private communications of both the Brazilian and Mexican presidents. The Brazilian government denounced the NSA surveillance as “impermissible and unacceptable,” and a violation of Brazilian sovereignty. As a result of US spying, Brazilian President Dilma Rousseff has postponed a state visit to Washington in October. See also: Venezuela asks UN to take action against US over visa dispute concerning the U.S. denial of visas for some members of the Venezuelan delegation who were scheduled to attend the UN General Assembly in New York.
‘Follow the Money’: NSA Monitors Financial World – (Spiegel – September 16, 2013)
The NSA monitors banks and credit card transactions — sometimes in apparent violation of national laws and global regulations. The European SWIFT financial transaction network is being tapped on different levels, internal documents from the US spy agency show. Classified documents compiled by the US intelligence agency NSA that deal with the activities of the United States in the international financial sector show how comprehensively and effectively the intelligence agency can track global flows of money and store the information in a powerful database developed for this purpose. “Follow the Money” is the name of the NSA branch that handles these matters. The name is reminiscent of the famous catchphrase by former FBI Associate Director Mark Felt, the whistleblower known as “Deep Throat” who offered the information to Bob Woodward and Carl Bernstein, the Washington Post reporters investigating the Watergate scandal in 1972. The main NSA financial database Tracfin, which collects the “Follow the Money” surveillance results on bank transfers, credit card transactions and money transfers, already had 180 million datasets by 2011. The corresponding figure in 2008 was merely 20 million. The classified documents show that the intelligence agency has several means of accessing the internal data traffic of the Society for Worldwide Interbank Financial Telecommunication (SWIFT), a cooperative used by more than 8,000 banks worldwide for their international transactions. The NSA specifically targets other institutes on an individual basis. Furthermore, the agency apparently has in-depth knowledge of the internal processes of credit card companies like Visa and MasterCard. What’s more, even new, alternative currencies, as well as presumably anonymous means of payment like the Internet currency Bitcoin, rank among the targets of the American spies.
LIFE STYLE/SOCIAL TRENDS AND VALUES
56% of Social Media Users Suffer from FOMO – (Mashable – July 9, 2013)
Social media can be an addiction, a slippery slope to a syndrome commonly referred to as Fear of Missing Out (FOMO). In fact, a new survey conducted by MyLife.com revealed 56% of people are afraid of missing out on events, news and important status updates if they are away from social networks. Many would trade other addictions to stay connected this way — about 26% percent said they would trade habits such as smoking cigarettes or reality TV for access to social networking sites. In the same vein, about 51% of people visit or log on more frequently to social networks than they did just two years ago. And users want their updates first thing in the morning: about 27% of participants flock to social sites as soon as they wake up. People are managing more social networking accounts as well. About 42% of study participants have multiple accounts — and the percentage jumps to 61% for those between the ages of 18 and 34. The average person also manages 3.1 email addresses compared with 2.6 from last year. Although 52% of respondents said they have considered taking a “vacation” from one or more social networks in the past year, only 24% said they will likely follow through. Why? FOMO, of course.
Death Be Not Decaffeinated: Over Cup, Groups Face Taboo – (New York Times – June 16, 2013)
In nearly 40 cities around the country, Death Cafes have sprung up in the last year. Offshoots of the “café mortel” movement that emerged in Switzerland and France about 10 years ago, these are not grief support groups or end-of-life planning sessions, but rather casual forums for people who want to bat around philosophical thoughts. What is death like? Why do we fear it? How do our views of death inform the way we live? Part dorm room chat session, part group therapy, Death Cafes are styled as intellectual salons, but in practice they tend to wind up being something slightly different — call it cafe society in the age of the meetup. “In Europe, there’s a tradition of meeting in informal ways to discuss ideas — the café philosophique, the café scientifique,” said Jon Underwood, 40, a Web designer in London who said he held the first Death Cafe in his basement in 2011 and has propagated the concept through a Web site he maintains. Mr. Underwood adapted the idea from a Swiss sociologist, Bernard Crettaz, who had organized “café mortels” to try to foster more open discussions of death. “There’s a growing recognition that the way we’ve outsourced death to the medical profession and to funeral directors hasn’t done us any favors,” Mr. Underwood said. He envisioned Death Cafe as “a space where people can discuss death and find meaning and reflect on what’s important and ask profound questions.” In practice, people’s motives for attending vary, as does the depth of the conversation. Dr. Tosiello, who said she had never lost a close family member, was there for intellectual enjoyment. Others went to ponder the questions and feelings that the death of a loved one had raised.
Translating Emoji into a Giant Light Show– (Vimeo – July, 2013)
Ancient Chinese texts and social media meet in a new giant light show at the Beijing National Aquatics Center. “Nature and Man in Rhapsody of Light at the Water Cube,” an installation created by artist Jennifer Wen Ma and lighting designer Zheng Jianwei, uses a computer program to translate the I Ching and the collective mood of the Chinese people into a stunning real-time light display on the building’s exterior. (“Emoji” is the Japanese term for the picture characters or emoticons used in Japanese electronic messages and webpages. Originally meaning pictograph, the word literally means e “picture” + moji “letter”. In the title of this article, it means roughly “collective emotional state”.)
CONTACT AND THE EXPLORATION OF SPACE
Scientists Find a Water-Rich Planet – (Forbes – September 9, 2013)
Japanese scientists have discovered a planet outside our solar system that most likely has a water-rich atmosphere. The planet, Gliese 1214b, is only 40 light years from Earth. Discovered in 2009, Gliese 1214b is what’s known as a “super-Earth” – bigger than Earth but smaller than a gas giant. In this case, it’s about 2.7 times bigger than Earth. Based on the original research after the discovery of Gliese 1214b, scientists were able to determine its mass, radius and density. But what still wasn’t known was the composition of the planet. Given the data, there were two major possibilities: first, that the planet was rocky, with a hydrogen atmosphere. The alternative is that the planet might be an “ocean world” comprised mostly of water. Based on the way light is scattered by particles that are smaller than the wavelength of light traveling through it, the most likely possibility is that the planet’s atmosphere is rich in water vapor. (There’s also a chance that it’s a hydrogen atmosphere with lots of clouds, but that’s less likely.)
DEMOGRAPHICS
Germans Export Grandma to Poland as Costs, Care Converge – (Bloomberg – September 16, 2013)
The “Grandma export” trend has set hands wringing in Germany, where Munich’s leading newspaper denounced it as “gerontologic colonialism” and compared it to nations exporting their trash. Yet more families say it’s their best option to provide a dignified old age for elderly parents—and save money—amid a lack of affordable quality care at home. One in five Germans would now consider going abroad for a nursing home, according to a survey by TNS Emnid, one of Germany’s biggest pollsters. Germany’s migrating seniors are an early warning sign of a challenge of global proportions. As birth rates drop, life expectancies increase and the baby boomer generation heads into old age, the United Nations estimates the world’s population of people older than 60 will more than triple to almost 2 billion by 2050. Meanwhile, even for seniors cushioned by government aid in countries like Germany, the cost of nursing home care is rapidly becoming prohibitive. German spending on long-term care for seniors is expected to increase from 1.4% of gross domestic product to 3.3% of GDP by 2060, the European Commission said in a report last year. (Editor’s note: From an economic standpoint, this practice is essentially exporting service sector jobs to a lower-wage country. If grandma is a U.S. citizen, how about visiting her every so often in San Miguel Allende, Lake Chapala or even Acapulco?)
Aging Boomers Befuddle Marketers Eying $15 Trillion Market Prize – (Bloomberg – September 17, 2013)
In 2017, approximately half of the U.S. adult population will be 50 and older and they will control a full 70% of the disposable income, according to data tracker Nielsen. By 2050, there will be 161 million 50-plus consumers, a 63% increase over 2010. Demographic trends abroad are even more pronounced: The number of Chinese people 60 or over is set to double by 2053. Globally, the spending power of consumers age 60 and older will hit $15 trillion by the end of this decade, up from $8 trillion in 2010, according to research from Euromonitor. Baby boomers, 8,000 of whom turn 65 each day in America, have reinvented each stage of life they’ve entered, from young adulthood to careers to parenting. And whether they’re working or retired, wealthy or on a fixed income, living alone or with other seniors, they aim to redefine what it means to be old. In 2011, the peak age of vehicle buyers shifted upward to 55-to-64 from 35-to-44, according to the University of Michigan Transportation Research Institute, and that trend is here to stay. Alison Sander, who runs the Boston Consulting Group’s Center for Sensing & Mining the Future, said “only about 5% of her corporate clients really understand the nuances of the senior market—it’s still a gray area” (pun intended?) for business. That helps explain why only about 15% of advertising dollars are spent on this demographic, despite accounting for almost half of consumer packaged-goods sales. When it comes to aging, myths abound. Here’s one: Older consumers buy the same brands they’ve always bought, so why bother catering to them? “If that theory was true, I would drive a Chevy Impala and wear English Leather,” said aging expert, Ken Dychtwald, 63. Myth number two: They’re one big group. Dychtwald separates the 50-plus market into four segments, based on their relative levels of activity and happiness: “Ageless Explorers” are youthful optimists, while “Sick and Tireds” are those in poor health and often with limited financial means. For more info on Dychtwald’s four types, including the “Comfortably Contents” and the “Live for Todays” see this link. For a complete overview of the research, go to revisioningretirement.com.

NEW TOOLS/NEW PROCESSES
‘Terminator’ Polymer Regenerates Itself – (Kurzweil AI – September 16, 2013)
Scientists have developed the first self-healing polymer that can spontaneously achieve healing in the absence of a catalyst. Self-healing polymers have been able to mend themselves by reforming broken cross-linking bonds, but that requires an external catalyst to promote bond repair, such as heat, light, or specific environmental conditions, such as pH. Ibon Odriozola at the CIDETEC Centre for Electrochemical Technologies in Spain used a poly(urea–urethane) elastomeric network, which completely mended itself after being cut in two by a razor blade. The metathesis reaction of aromatic disulphided (which naturally exchange at room temperature) enabled the regeneration. David Mecerreyes, a polymer chemistry specialist at the University of the Basque Country in Spain, sees opportunities to use this elastomer to improve the security and duration of many plastic parts, for example in cars, houses, electrical components and biomaterials. Future work by the group will concentrate on stronger polymeric materials; the current poly(urea–urethane) composite is relatively soft.
PROVOCATIVE IDEAS
The ‘Wild Dog Whisperer:’ Rescuing Wolves in California – (Yes Magazine – September 27, 2013)
This short documentary takes you into the world of Tonya Littlewolf, a Native American woman who started a sanctuary for wolves in California’s Lucerne Valley. Littlewolf has rescued wolves all her life. At a sanctuary in the California desert, she looks after 14 majestic wolves which have been rescued from breeders. Yet, as she cares for the creatures, even feeding them mouth-to-mouth, Littlewolf questions whether these wolves would be better off in the wild. Littlewolf speaks about her bond with the wolves and their significance in her life and culture.
FOR WHAT IT’S WORTH – articles off the beaten track which may – or may not – have predictive value.
Have-Nots Squeezed and Stacked in Hong Kong – (Bamboo Innovator – September 27, 2013)
On the first floor of a hulking residential building, at the end of a dimly lighted corridor, a narrow door opens up into Hong Kong’s economic underbelly. Twenty-two men live in this particular 450-square-foot apartment in the neighborhood of Mong Kok, in cubicles each hardly larger than a single bed, stacked above one another along two narrow passageways that end in a dank toilet and shower room. Each cupboardlike cubicle has a sliding door, a small television, some shelves and a thin mattress. Most of the men have lived here for months, some for years. Hong Kong’s per-capita gross domestic product is higher than that of Italy, and not far short of those of Britain and France, according to World Bank figures. But for unskilled or semiskilled people like Mr. Ng, the city is a tough place to be, said Wong Hung, an associate professor at the Chinese University of Hong Kong specializing in urban poverty and employment. Hong Kong’s economy underwent a major change in the 1980s, when much of the manufacturing activity that made the city famous in the 1950s and ’60s moved across the border to mainland China. In its place came banking, insurance, trading, logistics and real estate — service sectors that now employ nearly 90% of the work force but that have been unable to absorb many less educated workers. At the same time, Hong Kong has some of the highest living costs in the world, a huge and growing burden on those at the bottom of the income ladder. See also: New York Times slide show and Where Home is a Metal Cage: Hong Kong’s Poorest Live in 6ft by 2ft Rabbit Hutches
JUST FOR FUN
Washington Conservatory at TEDMED – 2013 – (You Tube – June 25, 2013)
120 fingers, 24 hands, 12 piano players – one piano!
A FINAL QUOTE–
The future is here. It’s just not widely distributed yet. – William Gibson, science fiction novelist
A special thanks to: Thomas Bergin, Bernard Calil, Steve Clayback, Ken Dabkowski, Ursula Freer, Anthony Judge, Thomas Kosbau, Matthew Lakenbach, Diane Petersen, Todd Pierce, Bobbie Rohn, Gary Sycalik, Steve Ujvarosy and all of you who have sent us interesting links in the past. If you see something we should know about, do send it along – thanks.
johnp@arlingtoninstitute.org
CONTACT US
Edited by John L. Petersen
johnp@arlingtoninstitute.org
www.arlingtoninstitute.org
PRIVACY POLICY: We don’t share your information with anyone.

